Smart Package Robot 's Encryption- and Hash-Function
Using GEC, you can make Smart Package Robot encrypt Messages for you. To make a long story short, Smart Package Robot supports unbreakable Cryptography, if you keep some rules.

Using GEC, you can make Smart Package Robot encrypt Messages for you. To make a long story short, Smart Package Robot supports unbreakable Cryptography, if you keep some rules.
There are many cryptographical algorhytmns out there with nice sounding names.
But there is only one of all these, that is scientifically unbreakable.
It is the so called "One Time Pad" (OTP).
Its mathematically proven, that a OTP is safe against cracking, as long as its done properly. Read more about a "One Time Pad".
In short, a OTP is a combination of your (prepared) message with a matrix of totaly random characters. We will however use the Term OTP also for the "Matrix of random characters" itself.
To use the OTP properly, these rules must be followed:
1.The OTP must only be know by you and be the receiver of the message
2. the OTP must have at least the size of the Message that is to be encrypted
3. the OTP must only be used once and then deleted on both sides
4. the OTP must be cryptographically random, this means that a "true random number generator" with a very long periode - or a hardware random number generator - must be used.
5. Your computer, as well as the computer from your contact, must not be compromised (Trojan etc.).
6. To delete the OTP, you need to use a safe method, not just the windows "Delete File".
For this purpose, we have included a "safe-erase file" in to the "DEL.-Command".
If any of these points above is not followed, the OTP may not be perfectly safe, see here:
Comment about deleting used "Pads":
As said, OTP's should only be used "once". Why?
Because once somebody can guess part of the content of a message, he can calculate the OTP and would then be able to decode all conversations.
Imagine an OTP as
There are mostly two standards to safely erase files,
1. The US DoD 5220.22-M standard (3-pass and 7-pass) -which is to weak for today.*
2. the Gutmann method, which overwrites the file with random data 35 times.
The SPR will beat both standards and add some passes to make sure your file is safely overwritten.
File-Buffering should be taken into account when using the SPR or any other of such tools.
Also if you use SSD's, they must never get into wrong hands, as a safe data-erase on SSD's may be a problem, due to the fact that the SSD internally tries to limit the write access to single blocks by exchanging them transparently against "blocks with less writes".. Which could lead to the fact that the blocks with the data may be left somewhere on the SSD, until the SSD is completely cleared.
Comments about the PRNG's in the SPR:
To make a unbreakable OTP-Encryption, we need a "Pad" of the highest possible quality.
To make sure, that the SPR meets all of these requirements, we have:
1. Included several Pseudo-Random Number Generator's (PRNG) into the SPR.
Any of these should be safe for cryptographical use. These PRNGs are integrated in the
! STR. - String Command and this way you have a choice which of these you use.
And nobody knows.
2. Of course you can and should test the Quality of your SPR generated Random Numbers here:
BATTERIES OF STATISTICAL TESTS FOR RANDOM NUMBER GENERATORS
but after submitting them to the Internet, don't use them any more - generate new OTP's
instead.
3. By just combining a OTP of a limited Bit-Range - like a Text - with a Full-ASCII-Range
OTP, the result may be statistically unsafe. Therefore the GEC-Command will first encrypt the
Message with the TEA-Encryption, and then use the unbreakable OTP.
This way, the Message has already a nearly perfect bit-distribution, before the OTP is used.
4. You can combine generated OTP's using the XOR. - XOR - Encryption. In fact this is done
internally already with STR.CHARS D and therefore of no need from as we see it.
If you decide to do so, use only Pads of highest cryptographicaly safe randomness.
Otherwise this may decrease the level of safety, rather then improving it. For details on
the used PRNG's see the ! STR. - String Command.
5. While we believe that the Random number generators that we use in the SPR are safe for
cryptographical use, we can supply a hardware-Random Number generator that uses
electronical noise to generate random numbers. If you need such a device you can contact us.
Other possible encryption methods
The SPR can apply normal Password-Protected Encryption using the TEA-Encryption scheme.
TEA is safe and generally fine when:
1. keys are random, this is the case if you use ! STR. - String Command. to generate the Keys.
2. the encrypted data is less then 1 GB
3. Safety is even better, if you use the optional "Bit-Flood" in the GEC.-Command.
Anyway for a maximum security against professionals, we can only recommend OTP's.
Here is an example on how to go:
1. Use the ! STR. - String Command to generate as many "One Time Pads", as you need for your communication. The SPR can easily create 1000'th of them in a Minute.
2. Share these "One-Time Pads" with your communication partner.
3. Use each OTP only one time (one day for example), next day - next Pad.
Think of these OTP's like your TAN-Numbers from the home-banking.
4. Have the OTP's numbered for each day in an month and use the OTP only on that day.
There is more ...
Using the SPR you can split large files of virtually any size into smaller files, using the
FIL.Split File - command.
And later you can join the small parts again to the original file, using
FIL.Join delete - command.
Also the above command will make an basic encryption of your splitted file with (default) 30 Rounds of TEA.
Then there is the "Byte-Flood"-Algo. Its implemented in the
HIT.-command.
This command can be used to make a fast XOR.-encryption without having a password.
Using "Byte-Flood", the file itself is been used as Encryption Matrix.
There are no secrets ...
All cryptographical technologies used in teh SPR are based on public available,
scientifically approved methods.Mostly based on direct machine-code of very short size.
Therefore the result of all algorhytms (TEA., XOR.,SHA., GMD. etc.) can be tested and compared to public sources.
Random Number generation...
Its like the generation of TAN-Numbers for your home-banking. Once an attacker would get an idea how you generate your numbers, he could theoretically calculate the whole periode of random numbers and try to guess them.
The bad news is that the time to calculate the whole periode of random numbers, we use in the SPR is theoretically about 1700 years on a Standard computer.
But now what we do is, we combine the resulting numbers (random times) with other generated numbers. The result is that even if somebody could "crack" our PRNG, he would need to also check a lot of combinations and the possible combinations of such a large sequence is quadratic to such a sequence. Now note that we do not only combine 2 such random "Pads" but 10 or 20 when using for example
STR.CHARS D
to generate a One-TIme-Pad.
The only alternative to this is, to use a hardware-Random Number Generator on a Computer that is not connected to any network.For companies who want the maximum safety, this is the system that we recommend for the OTP-(Random Number) Generation.
The "Random Numbers" (OTP's) can then be given to company members via USB-Sticks or on a CDR. We can supply such a Hardware RNG, please contact us if you are interested.
How can you make your own perfect OTP's?
The perfect OTP-Generator is a Computer that is not connected to a network.
It will just be dedicated to the Generation of OTP's and store them on USB-Sticks.
If possible, it will use a hardware random device. However ... our Software PRNG's are also very good. And at the time of this writing i have no reason to assume that anybody in the world could guess their random number sequence with actual technology.
How fast does the SPR create "OTP"'s / random numbers?
We have used the script below to generate random numbers using all four PRNG's
'
'SPR Script-file: PAD-Sample
'Purpose:
'Author: Theo
'Creation date: 11-19-2014 at 13:24:40
'===========================================================
' PAD-Size 1 Mrd. Byte
$$NUM=5E8
VAR.$$LET=A
GSB.create_pad
VAR.$$LET=B
GSB.create_pad
VAR.$$LET=C
GSB.create_pad
VAR.$$LET=D
GSB.create_pad
MBX.Ready
ENR.
:create_pad
VBT.$$LET
FOR.$$CNT|1|3
GSB.make_pad
NEX.
RET.
ENR.
:make_pad
VAR.$$TIA=#dtime#
VAF.$$FIL=?pfad\PAD_$$LET$$CNT.txt
$$PAD=
STR.CHARS $$LET|$$NUM|$$PAD
VAR.$$TIB=#dsince#
CTF.$$FIL|$$PAD
VAR.$$TIC=#dsince#
VAR.$$TXT=STR.CHARS $$LET needed $$TIB seconds to$crlf$ create the Pad of $$NUM Bytes. $crlf$ Additionally $$TIC sec. for writing the Pad to HD).$crlf$
PRT.$$TXT
RET.
ENR.
'===========================================================
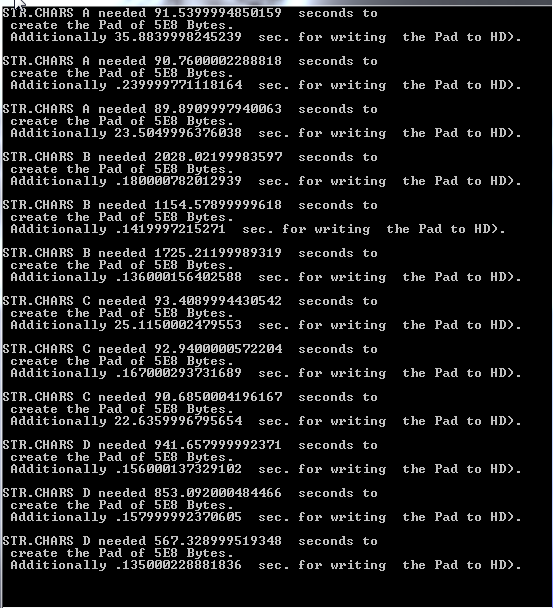
The picture below shows the time in seconds, for the generation of 500 Million Random Numbers using all four algos. As you can see, Algo "STR.CHARS B" is the slowest.
That is because he will internally generate 20 "Random Pads" and combine them.
The next slowest Algo is "STR.CHARS D", he will combine about ~5 Random Pads.
You can however get a OTP of 500 MB in 1 and a half Minute, using the "STR.CHARS A" Algo.
How good are our random numbers?
To Test Random Numbers there are several Methods out there,
One of them is the so called "ENT-Test Suite".
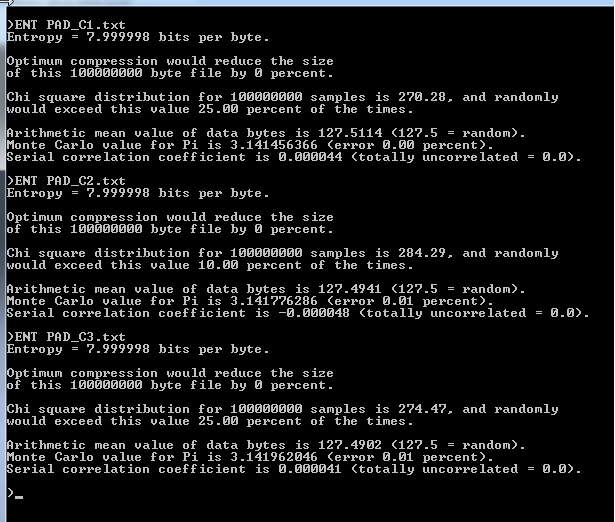
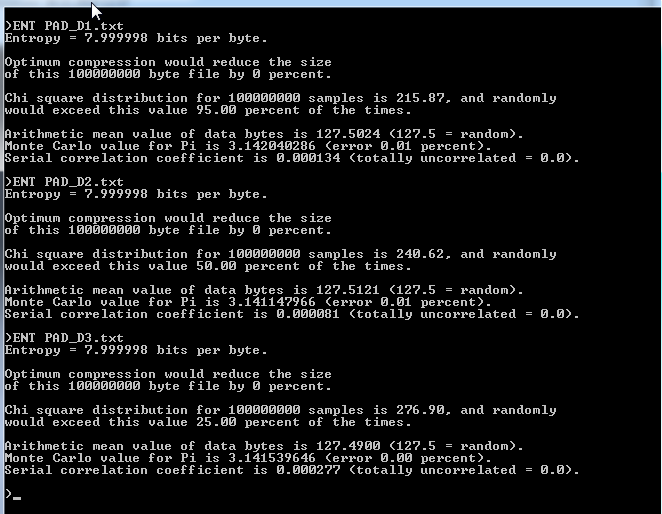
We could not use this suite on our 500 MB Pads because the ENT Programm was unable to handle data of this size. SO we created smaller Pads of 100 MB.
Note that these numbers below may not be perfectly accurate because there were other processes running on the test computer in the background.
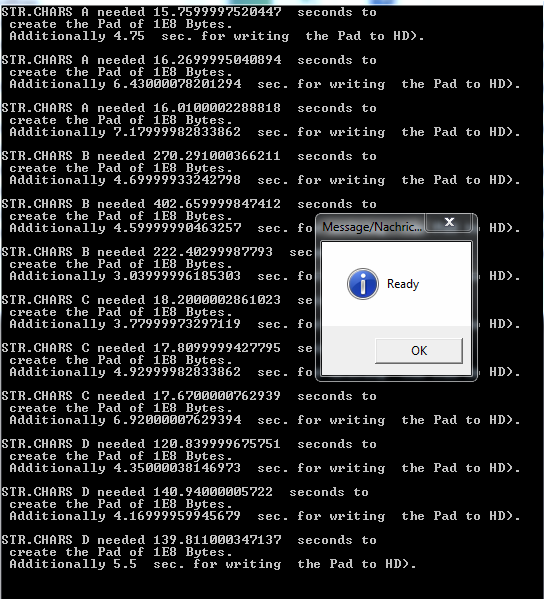
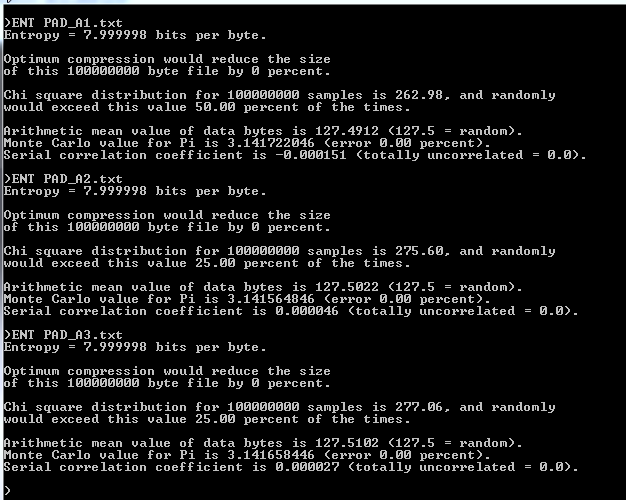
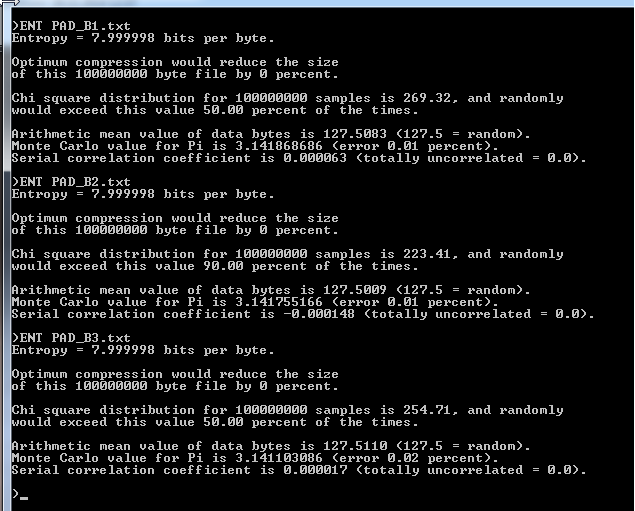
Next we tried the "ENT-Suite" on our 100 MB OTB's.
Here is the result.
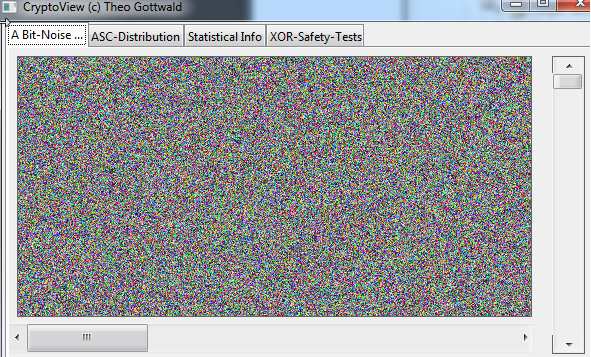
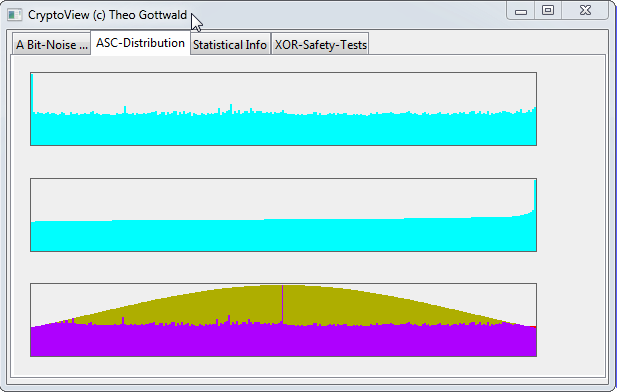
We will supply also a new tool together with this version of the SPR: "Crypto-View".
Using Crypto-View you can identify non perfect random distributions more easily.
Lets first take a look on our Pads in "Crypto-View".
This is how it should look: "totally noisy".
On the second TAB "ASC-Distribution", you should see a GAUSS-Curve in the third picture,
The larger the OTP-file, the less "round". Here are two examples of SPR generated OTP's.
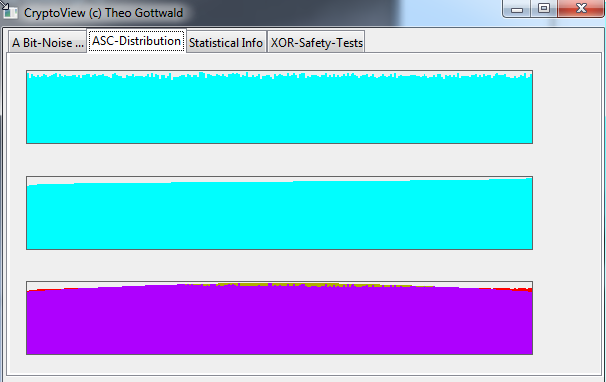
This is a "Crypto-View" from an OTP of about 500.000 Bytes.
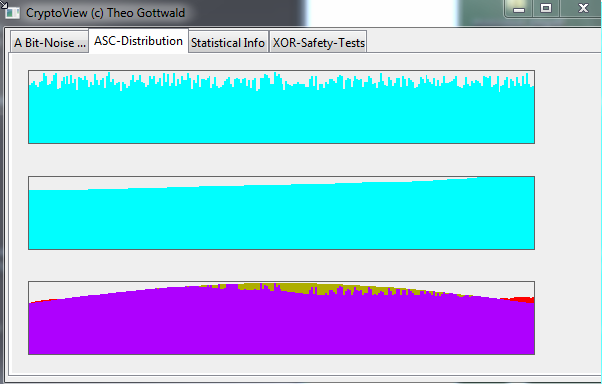
This is a "Crypto-View" from an OTP of about 50.000 Bytes. Of course with such smaller files, the distortion is more clear visible.
Lets take a look on a file that is not perfectly distributed. A ZIP-Archive for example.
You can drag and Drop it on Crypto-View. Watch out for these horizontal lines. They tell you ... its something else.
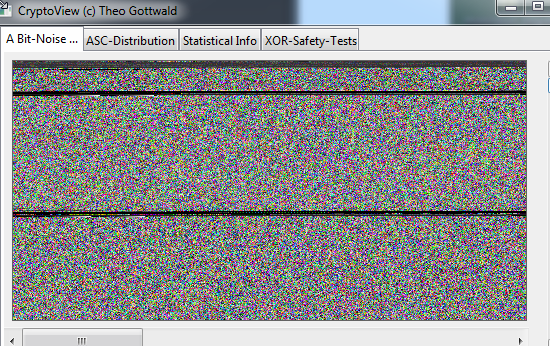
This is a PDF-File.
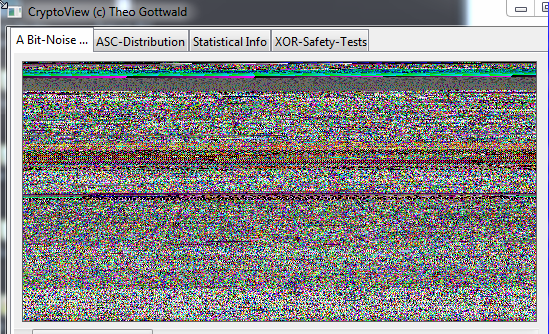
This is an executable. You see the "lines" sometimes more clear - sometimes less clear (with larger files). If you move the slider on the right side downwards, the colors may change and get a red, green or blue "touch". If that happens - its NOT RANDOM.
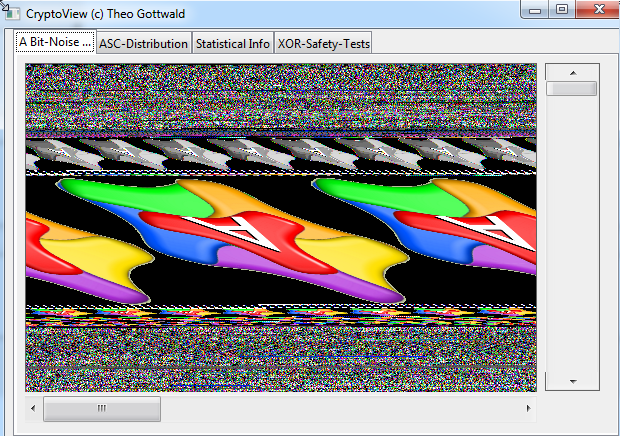
This is the Crypto-View of an SPR-Executable-File. As you can see the most space is used by the new modern Icon-Look. And the rest contains some horizontal lines, which identify it as "Non-random".
The easiest way to sort bad Random numbers out, is to watch for the Gauss-Curve.
What is a Gauss-Curve?
You know that story.If you have a shop, long time no customer comes ... and then they come all at once. Just if they had an appointment at that time. Thats a so called "Gauss-bell".
Its just "random distribution". The same happens in true Random numbers.
With very large files you get more and more straight lines and the curve is not so good to see.
But you will always know when its a Gauss - or not.
For example ... this below is not a Gauss (red lines).
If its not a ... more or less ... Gauss ... its not a true Random File.
The SPR is a Cryptography Construction Set
You can generate your own Encryption-System using the SPR.
You can compile it and use it.