MiniRobotLanguage (MRL)
XOR. Command
XOR Encryption

Intention
Logical operations on Bit-Level. Combines/Encrypts or decrypts Bit-Patterns.
Works from a string or a file, to a string or a file.
While the name of the Command is just "XOR." this command knows all possible encryptions-on-bit level.
You can choose from the following logical operations to encrypt or decrypt any Plain-Text on Bit-Level:
- XOR (default option or "x")
- ADD/SUB (Option "a")
- ROL/ROR (Option "s")
- Byte-Flood
And you can even combine all of them just as you like in a single command.
This command uses a "Pipelined architecture" therefore you can apply all of the above options with a single command. Then all Options will be applied with the same KEY on to the same Clear-Text. One after the other, In the right Order - which is important for decryption.
We will take a look on what happens with a Message when being decrypted.

$$FIL=?path\Western.txt
$$OUT=?path\Crypted.txt
$$KEY=1-+rDsdf/(klsdaf
' We encrypt "file to file"
XOR.efo|$$FIL|$$KEY|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
XOR.dfo|$$OUT|$$KEY|$$NEW
ENR.
![]()
To make sure that we do not have a pure "character substitution", the command offers additional features (Byte-Flood).
This will help especially with short keys, if there is a chance that somebody will try brute force to crack your Cryptography.
XOR. with a weak and short Password is far from being a safe method.
It becomes safe, in combination with a "One Time Pad" that has the size of the code that is to be encrypted.
Let me show this to you with an example:
$$OUT=?path\Crypted.txt
$$KEY=1
$$TEX=bbbbbbbbbbb
' We encrypt "file to file"
XOR.eo|$$TEX|$$KEY|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
XOR.dfo|$$OUT|$$KEY|$$NEW
ENR.
Will produce this crypted text:
![]()
you can still make assumptions on the source-code.
Of course this will get better if we use a more complex $$KEY.
But first lets try this addition to XOR:
$$OUT=?path\Crypted.txt
$$KEY=1
$$TEX=bbbbbbbbbbb
' We encrypt "file to file"
XOR.3eo|$$TEX|$$KEY|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
XOR.3dfo|$$OUT|$$KEY|$$NEW
ENR.
The result we get is this, and this is at least a few bits better.
![]()
Note that there is a chance that Passwords can become visible when using XOR. and Bit-Flood in an unlucky way and with difficult Plain-text. Like in this case:
$$OUT=?path\Crypted.txt
$$KEY=Ralf
$$TEX=bbbbbbbbbbb
' We encrypt "file to file"
XOR.2eo|$$TEX|$$KEY|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
XOR.2dfo|$$OUT|$$KEY|$$NEW
ENR.
![]()
Therefore check the result of your operations in a HEX-Editor.
Or better use only cryptographical safe Passwords that make no sense when using XOR.
Of course the best way is to first use GEC. and then add up something else.
Best use a real "One Time Pad".
The usage on strings is simple:
' Combine $$TXT and $$KEY
XOR.e|$$TXT|$$KEY|$$TXT
' This way you can save the result as file immediately.
' Combine Variables into a file
XOR.do|$$TXT|$$KEY|$$FIL
XOR.efo|$$FIL|$$KEY|$$FIL
' This example loads a file and places
' the result into a variable
XOR.ef|$$FIL|$$KEY|$$TXT
What happens, if the $$KEY is shorter or longer then the $$SRC
In either case, the XOR COmmand will handle the situation automatically.
To long $$KEY's will be shortened internally before beeing used. And if $$KEY is shorter then t$$TXT, the $$KEY will be repeated as often as needed to fill the gap.
For example:
$$TXT=Hallo Leute
$$KEY=12
' Then XOR will repeat $$KEY and use internally:
$$TXT=Hallo Leute
$$KEY=12121212121
While this will definitely make the text unreadable, it is far from bullet-proof encryption.
XOR-Encryption alone may under several circumstances not lead to professional security, therefore we recommend to use the GEC.-Command for encryption.
The XOR. can be used to combine Random Numbers of different sources to a single result.
If you just want to hide something, you can use the HIT.-Command.
Do multiple XOR's make the result more secure?
No, as mathematically all XOR's can be shortened to a single XOR Operation.
Its just like an addition ... many additions can be shortened to a single addition.
However if you additionally use the ADD/SUB or ROL/ROR and the "Byte-Flood", the result will be hard to beat.
How can i make a definitely scientifically proven safe encryption that is unbreakable?
The only way is to use a so called "One-Time Pad". That is a "Key-File" with Random Data Bytes, that is only available to you, and tot the receiver of the message.
Then I recommend to use first GEC. on any important Plain-Text Message - just to make a statistical Binary from your Plain-Text.
And after that apply XOR. with some of its Options and a "Random Pad Key" that you have generated using the STR.CHARS D command. Doing so the result is mathematically unbreakable as long as the sender doesn't get hands on the decryption key.
Then make 500 Pads on a USB-Stick and give the stick to your communication partner.
So he can use every day a new "Pad" and delete the old Pad.
This way the message can never in the future be encrypted any more.
To help you about this we have now a included a "Safe-Erase" for "Pads" in the DEL.-Command. It will overwrite the Pad 40 times with Random Data before deleting it.
Making as sure as possible that your messages will stay private to you and the receiver.
What is most important when encrypting with XOR?
The most important point is the quality of the used PRNG for the Encryption Key.
For Details about it see ! Smart Package Robot 's Encryption and Hashing Commands
Making your own Encryption System
Using XOR. and GEC. the SPR is a "Crypro-Construction Set".
Making things as easy for you as possible. However there is something for you, to care about. In case you want to construct your own Encryption/Decryption using multiple
XOR.-Commands please note the following rule:
Plain-Text -> XOR.KEY1 -> XOR.KEY2 -> XOR.KEY3 -> Ciphertext
must be encrypted in reverse Order like this:
Ciphertext -> XOR.KEY3 -> XOR.KEY2 -> XOR.KEY1 ->Plain-Text
You only need to worry about this if you use multiple XOR./GEC. Encryption Commands in a chain. If you use just one command with multiple Options, they will internally be sorted in a way that it will work as expected.
By varying the prototypes between the given options, you always get different Ciphertexts. Below some Ciphertexts all from the same Plain-Text. All with just one XOR.-Command.
Technically the "d" - decrypt - Option is always the reverse of the "e" - encrypt option.
Therefore you can also use "d" for encryption and in this case "e" for decryption.
The ciphertext will in this case look different from the normal results.
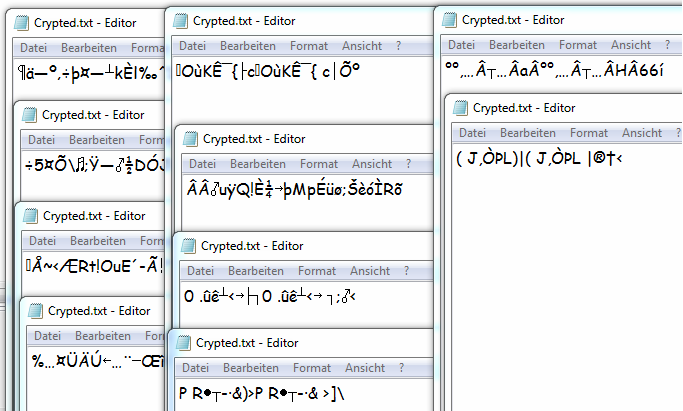
This picture shows some possible Ciphertexts, all from the same Plain-Text. All with just one XOR.-Command and changed prototypes.
What is most important when encrypting with XOR?
The most important point is the quality of the used PRNG (Noise-Overlay/ the One-Time-Pad) for the Encryption Key.
For Details about it see ! Smart Package Robot 's Encryption and Hashing Commands
Speed considerations:
On a typical test-system, a file with 17.8 MB is encrypted with lowest strenght in 0.3 seconds. The decryption of the same file takes about 0.2 seconds. Note that for most use-cases, this level is all you will ever need.
The same file is been encrypted with standard strength (140 Rounds) in about 1.9 seconds. The decryption for that file takes 1.7 seconds.
The same file is been encrypted with highest strength (level 9) in about 12.8 seconds. The decryption for that file takes 12.3 seconds.
Syntax
XOR.P1|P2|P3[|P4]
Parameter Explanation
P1 - VAR/Prototypes
P2 - VAR with the String or the Filename to process
P3 - VAR with Key to en-/decrypt
P4 - (optional) VAR with Filename or Variable for the result, if omitted, result goes to TOS
Prototypes must be lowercase letters like following:
f -input from file - if f is not specified, the Variable is been resolved to a string.
e - "Encrypt". If e is not specified the input is been decrypted.
o - output result to a file. if o is not specified, output is directed into the variable P3, or if none to the TOS.
s - (Shift Operation) "ROR"/"ROL" - used together with "e" it will use the
"ROR" (Rotate Right) algo. Used together with "d", this will use the
"ROL" (Rotate Left) algo. "ROR" and "ROL" are complementary operations.
Each can be used to decrypt the other, or to encrypt for the other operation.
a - "ADD"/"SUB" - used together with "e" it will use the "ADD" algo. Used together with "d",
this will use the "SUB" algo. "ADD" and "SUB" are complementary operations. Each
can be used to decrypt the other, or to encrypt for the other operation.
x - (default if no "s" or "a" is specified. Will use XOR-Encryption/decryption.
If "s" or "a" was specified, then "x" must be given to additionally use XOR.
Numbers from 1 to 4 add the "Byte-Flood Algo".
This will additionally shift Bytes around to confuse the result.
While for normal XOR-Operation, the Use of "e" is optional, in case of using "Byte Flood", the use of "d" or "e" are necessary to get the wanted result.
0 - Do a single "Byte-Flood-Round".
1 - Do as Many Rounds as the Target has Bytes.
2 - Do 5 times the Rounds as the Target has Bytes.
3 - Do 6 times the Rounds as the Target has Bytes.
4 - Do 8 times the Rounds as the Target has Bytes.
Example
'******************************************************************
' XOR-Sample
'******************************************************************
'
' We encrypt "file to file"
$$FIL=?path\Western.txt
$$OUT=?path\Crypted.txt
$$KEY=1-+rDsdf/(klsdaf
CFF.$$FIL|$$PLA
XOR.eo|$$PLA|$$KEY|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
XOR.df|$$OUT|$$KEY|$$PLC
' Save it to a file
CTF.$$NEW|$$PLC
ENR.
'******************************************************************
' XOR-Sample 2
'******************************************************************
$$FIL=?path\Western.txt
$$OUT=?path\Crypted.txt
$$KEY=1-+rDsdf/(klsdaf
' We encrypt "file to file"
XOR.efo|$$FIL|$$KEY|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
XOR.dfo|$$OUT|$$KEY|$$NEW
ENR.
'******************************************************************
' XOR-Sample 3
' Single Character XOR
'******************************************************************
' A - 65 - 01000001
' 1 - 49 - 00110001
' XOR================
' p 112- 01110000
' 1 - 49 - 00110001
' XOR================
' A - 65 - 01000001
'
VAS.$$KLA=A
VAS.$$KEY=1
PRT.Klartext=$$KLA
XOR.e$$CNT|$$KLA|$$KEY
PRT.Verschlüsselt: $$KLA
XOR.d$$CNT|$$KLA|$$KEY
PRT.Klartext=$$KLA
MBX.!
ENR.
Remarks
XOR. is provided to enable you, to apply mathematical XOR on any amount of Data.
To generate an encrypted "One Time Pad", we recommend that you rather use the GEC.-Command.
To use the encrypted characters in Chat-Programs or e-mail, do not forget to use the
STR.TEXT TO MIME before,
Of course the encoding must be reversed on the other side before decryption.
Limitations:
1. File-Size
The actual Implementation tries to load the complete file into Memory before applying the Encryption. Therefore Files with a size that exceeds the Systems RAM Capabilities can not be encrypted or decrypted. In case there are File-Errors, an empty string is returned.
See also: