MiniRobotLanguage (MRL)
HIT. Command
Hide Text using the "Byte-Flood" Algo

Whats hidden in this pictures?
Intention
This command offers a very basic encryption, by XOR'ing a Text with an internal 250 Byte hardcoded Pad. Also it will do an XOR with the neighbour Byte ("Byte Flood") and therefore make things definitely unreadable.
The advantage is that it does not need a Password, because it uses the internal Pad and the Data itself as "Key".
Note that this algo alone is not safe encryption, because anybody who owns the SPR can decrypt it!
It shall only be used in combination with other commands like XOR and GEC..
It can also be used if you just want to hide something and make it unreadable.
I recommend this algo as a part of a private encryption scheme, not as a standalone encryption.
You can influence the number of rounds by choosing an appropriate selection of prototypes. Unlike with XOR. - XOR - Encryption , the "Byte Flood" encryption and decryption use separate algos, therefore you need to choose "d" or "e" depending on what you are doing.
Here is an example, before and after using :
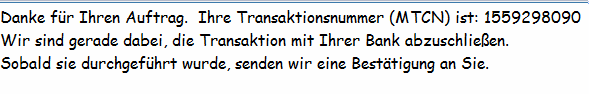
We use a Script that produces an encrypted file:
$$FIL=?path\Western.txt
$$OUT=?path\WesternC.txt
HIT.efo0|$$FIL|$$OUT
![]()
This is just a part of the result. And its definitely unreadable.
This way you can send the Western Union code safely.
While do not use it for the new important new developments of your company.
Because anybody who owns an SPR can decrypt it. This is the decryption script:
$$NEW=?path\Receiver.txt
HIT.dfo0|$$OUT|$$NEW
HIT. will not fail fail even on diffcult Plain-Texts, due to the used hardcoded Pad.
Therefore in the actual implementation, 0 rounds is completely safe.
A higher number of Rounds produce other results.
If you use more then 0 rounds, check the result. For example, take this Plain-Text:
![]()
Crypted with a Single Round HIT., it will look like this:
$$FIL=?path\Difficult.txt
$$OUT=?path\Crypted.txt
HIT.0ef|$$FIL|$$OUT
![]()
Does not leave any wishes open so far. Lets see what happens if we increase number of rounds. Now the result from this:
HIT.efo2|$$FIL|$$OUT
looks like this:
![]()
A simple
HIT.efo2h|$$FIL|$$OUT
would have this result:
![]()
Generally HIT. is an additional tool to quickly make stuff unreadable.
Its not an unbreakable encryption.
Back to decryption. Note, that we have used the "2h" and that if we use it for encryption,
we must use the same parameters for decryption!
' We decrypt it like this
$$NEW=?path\Receiver.txt
HIT.2hdfo|$$OUT|$$NEW
ENR.
Looks like HIT. can get a good result with difficult Plain-Texts.
To get a much better result, we can add a fix Pattern in front of the message.
The longer, the better.
Doing this, the result can only easily be decrypted from somebody who knows that Prefix.
Is it safe?
Possibly not. But its good for hiding Text. Thats why the name os "HIT."
Here is an example:
' We encrypt "file to Variable"
$$FIL=?path\Difficult.txt
$$OUT=?path\Crypted.txt
$$PRE=1-+rD
CFF.$$FIL|$$PLA
' Add a Prefix for better encryption
VAR.$$PLB=$$PRE$$PLA
HIT.1eo|$$PLB|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
' We encrypt "file to Variable"
HIT.1df|$$OUT|$$PLC
' Remove $$PRE from Result
GSS.6|0|$$PLC|$$PLD
' Save it to a file
CTF.$$NEW|$$PLD
ENR.
On the other side ... who needs a Message like "aaaaaaaaaaaaaaaaa"?
If you have difficult Plain-Texts, i recommend to combine multiple systems,
for example GEC. and XOR. (one time Pad).
HIT. is for hiding unimportant stuff, where you do not need to remember a Password.
New Option: Super-Hide.
This Option is even more safe, because the result of "Hiding an Text" will never be the same!
Therefore if you run the Script 5 times. You will get five different result.
This increases the safety of the result - especially against Brute Force attacks..
$$KEY=Alles neu macht der Mail!
FOR.$$LA3|1|5
HIT.2se|$$KEY|$$CRY
DBP.Crypted: $$CRY
' We decrypt it like this
HIT.2sd|$$CRY|$$NEW
DBP.Decrypted: $$NEW
NEX.
ENR.
Now here is what we get, as you see there are 5 completely different results for the same Input:
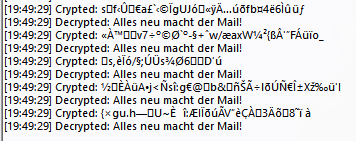
You will never (maybe 1 in a Billion times?) get the exactly same result in this type of Super-Hiding.
Therefore a Brute Force attack is near to useless.
Syntax
HIT.proto|P1[|P2]
Parameter Explanation
P1 - VAR, Filename or String to encrypt.
P2 - (optional) - VAR for Return value. If omitted, TOS is used.
The following prototypes can be used:
f - if given, then P1 is a filename, not a Text-String. If omitted, the content of P1
is taken.
o - if given, then P2 is a filename, not a Variable for ther result.
If omitted, the content of P2 is treated as a variable where the result shall be stored.
If P2 is omitted, then the result is been placed on TOS.
If "o" is specified, then a filename for the result-file must be given!
z - multiply number of rounds times 10.
m - multiply number of rounds times 100.
h - multiply number of rounds times 500.
s - Use "Super-Algo" (slower!) that will add an additional Hiding-Level that makes the results never look equal.
e - signals that the encryption-algo shall be used.
d - signals that the decryption-algo shall be used.
Numbers from 0 to 9
0-9 You can specify numbers from 0 to 9 to specify the number of rounds
that should be done.
Example
'******************************************************
' HIT. - Sample
'******************************************************
' We encrypt "file to file"
$$FIL=?path\Western.txt
$$OUT=?path\WesternC.txt
HIT.efo|$$FIL|$$OUT
' We decrypt it like this
$$NEW=?path\WesternD.txt
HIT.dfo|$$OUT|$$NEW
ENR.
'******************************************************
' HIT. - Sample #2
'******************************************************
' We encrypt "file to Variable"
$$FIL=?path\Difficult.txt
$$OUT=?path\Crypted.txt
$$PRE=1-+rD
CFF.$$FIL|$$PLA
' Add a Prefix for better encryption
VAR.$$PLB=$$PRE$$PLA
HIT.1eo|$$PLB|$$OUT
' We decrypt it like this
$$NEW=?path\Receiver.txt
' We encrypt "file to Variable"
HIT.1df|$$OUT|$$PLC
' Remove $$PRE from Result
GSS.6|0|$$PLC|$$PLD
' Save it to a file
CTF.$$NEW|$$PLD
ENR.
Remarks
To use the encrypted characters in Chat-Programs or e-mail, do not forget to use the
STR.TEXT TO MIME before,
Of course the encoding must be reversed on the other side before decryption.
Limitations:
Possible maximum file-Size is limited by System RAM, and generally to a maximum of 1-2 GB (32 bit).
See also: