Compiler-Directives
#CRY: - Encrypt Scripts on Disc
Used to encrypt the Scripts that are stored on Disc to make them unreadable.
Intention
When you have a Script you will often compile it to an EXE-File. This EXE-File may be given to Clients or Customers.
Now when the EXE-File is been started, it will make a "Quick Install" in the Temp-Folder of the Client-PC.
It will unpack all the Scripts as well as included Setup-Files. Generally you can see this Project in the Temp-Folder as an
~Temp(unique number) somewhere. Here is an example:
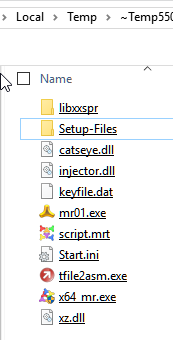
Now somebody could "steal" your code-algorithm or included Passwords, by just opening the file inside the SPR-Editor, or even Notepad.
To make this very heavy (yet nothing is impossible in the world of hacking today) we have included the
'#CRY: - Directive
If you specify this anywhere in your code (can also be in a Library-File), ALL ".mrt"-Script-files will be encrypted.
How can i check if my Scripts are really encrypted?
You can check if your Scripts are encrypted, by adding these statements at the Top of your code:
EXO.?path\
MBX.!
Now you compile the Script and Run the compiled EXE-File.
Once these commands are executed, the Script will open its folder, which may look similar like this:
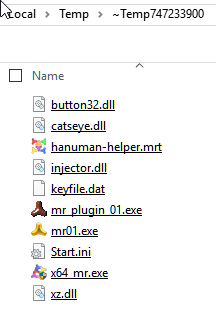
Now just double click on the Script-File and load it into the Editor. You may see something like this:
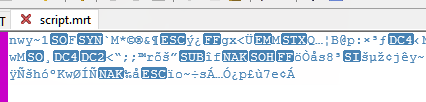
If its completely unreadable then your Script is crypted. You will NOT be able to recognize ANY WORD that was in the Script before.
Now we are going to take a look on some encrypted Scripts to give you an impression of the Encryption.
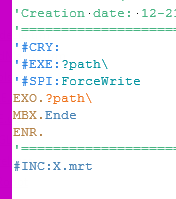
We are going to use the following Script. This Script will "include" the small Script "X.mrt" via
#INC:X.mrt
For Details on the Preprocessor-Include see here: 1.1 #INC: - Pre-Processor File-Include
Now this is the Main-Script:
Here is the Original "X.mrt" in the Editor. As you can see its just 3 Bytes long.
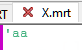
Now we compile the Script and start it. The Script will then open its temporary Folder and show us the unpacked Script-Files.
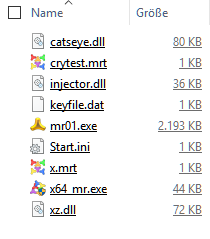
Now I am going to open the "X.mrt"-Script-File. It looks like this:
![]()
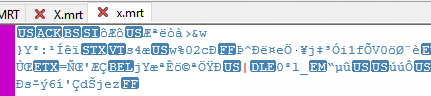
Ok, I will do the same again. NO CHANGE in the Code. Just take the same Script and compile it again.
Will it look equal? No, this time it looks quite different.
Ok, lets do it a third time. Compile ... and run. Open "X.mrt" in the Editor.
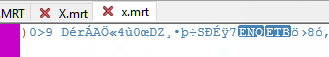
Even the third time it looks totally different. Here are some Keypoints about the used Encryption-Scheme.
Now we will check something else.
We will now use this file as "X.mrt". How will the encrypted version look?
The first thing we need to know is, that the "Original file" has a size of 4826 Byte.
See below.

After Encryption the size of the file has reduced to 788 Byte.
From this example, you can see that the internal Algo will also remove redundancies before doing an Encryption.
Now here is how it looks after encryption:
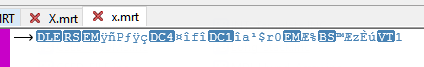
You will not have any idea how it looked before, or even how long the original file was before.
Here are some Points about the internal Encryption Algo.
1.. Code is Compressed to reduce Redundancies
2. Code is Padded to fixed sizes.
Therefore, what you can see is that there are no valid conclusions about the original Code-Size.
3. Code is encrypted in an way that can mathematically not be reversed other then using the code that is inside the SPR it self..
YOU CAN TRUST the Encryption of the '#CRY: - Directive that it will definitely hide your Passwords very well.
Nothing that was readable in the Original Code will be readable in the Encrypted Code.
We added a improved Version of "CryptoView" to this SPR, and it will show you that any statistical Method of cracking the Script-Files is likely going to fail.
Having said this, there is no 100% Warranty that nobody will be able to find and extract the loaded Script in Memory or
use the built-in routines via Code-Hacking. However only Professionals with a lot of time and Know-How will be able to succeed in this.
And they need to have the SPR also.
Hint: You can use the '#CRY: - Directive together with the JNF.-Command as well as with the #INC: - Preprocessor-File-include.
Syntax:
'#CRY:[P1]
P1 - Can only be a 0 or a 1. if omitted a "1" is used and this says that the code shall be encrypted.
Actually there is no way to encrypt only a few scripts. Using '#CRY: or '#CRY:1 will always encrypt ALL SCRIPTS in a compiled package.
In the same way, if there is a '#CRY:0 in the code, this will switch OFF Decryption for ALL Scripts.
If there are multiple such statements found, the LAST statement will be the one that counts.
Example:
'----------------------------------------
' Test if your Script is crypted
' compile this and run the EXE-File.
' then
'----------------------------------------
'#SPI:ForceWrite
'#EXE:
'#CRY:
'
EXO.?path\
MBX.!
END.
Parameter Explanation:
-
Remarks:
Preprocessor-Directives start with the Sequence: #
Because this is only important for the Preprocessor, the running script ignores these commands at Runtime (at time of script execution).
Limitations:
How SAFE is the crypted Script-File and contained Passwords etc.?
About giving the file to somebody and say "please decrypt it" is mathematically impossible as we see it.
We have used protected ASM code therefore this is the maximum Level of safety.
However we see the following possible Safety problems:
1. Decryption is possible only when using the built in decryption subprograms that are contained somewhere in the Robot's internal code.
The only ways a potential Hacker could get the content of the Script-code is:
a) To hack a program to get to its internal data is theoretically possible with any program out there,
And the SPR- even though there is some protection - can not make an exception to this.
b) If somebody can get hands on the SPR-Source code (buying the Company :-))
he may be able to decrypt Scripts.
2. If you need to make a compiled Script readable AND if you can proof that YOU are the valid Owner of the Script,
AND if you can pay some days of work-time, WE here at the SPR-Development can also make encrypted Scripts readable again.
For this we would need to compile a special version of the SPR which is actually nowhere available.
These are the the only ways we see, to get hands on the Script-Code. None of these will be easy or cheap.
We believe that, any statistical attack on the encrypted code will fail.
See also:
• 2.1.8 '#INC: - Include Files and Folders into the Executable
• 1.3 '#SPI: - Special Instructions
• #ONCE / # OEND - Multiple Include Protection
• 1.1 #INC: - Pre-Processor File-Include
See further:
•2.1.2 #AOS: - Choose valid OS for executable
•2.1.3 '#EXE: - Set Executable Path and Name
•2.1.4 '#EXV: - Execute on System Desktop
•2.1.5 '#HID: - Hidden Desktop Scripts
•2.1.7 '#SPI: - Special Instructions
•2.1.8 '#INC: - Include Files and Folders into the Executable
•2.1.9 '#EXC: - Exclude Files or Dirs from Executable
•2.1.A #LIB: - User-Library Path
•2.1.B #CRY: - enCrypt the Script
•2.1.C '#AFT: - Run AFTER Compile
•2.2.1 '#ICO: - Choose own Icon
•2.2.2 '#ICF: - Icon from Icon-Folder
•2.2.3 '#ICS: / '#ICS: Icon-Set
•2.3.0. '#MAN: - Manifest for Executable
•2.3.1. '#MAU: - UI-Access for Manifest for Executable
•2.4.0. '#VER: - Version-Informations
•2.5.0. '#CIL: - Direct Compiler Interface